Draft CMMC v0.4 Has Been Released
Published:
Sept. 6th, 2019
The Wait is Over.
The mid-point release of the CMMC standard is out in draft for a limited time.
We can finally see what the standard is shaping up to look like. The DoD has released the draft in an effort to gain industry feedback on the model. This is the first of three drafts that they plan to release. Draft CMMC v0.4 will be available until September 25, 2019 for feedback and review.
The Official Draft is available here.
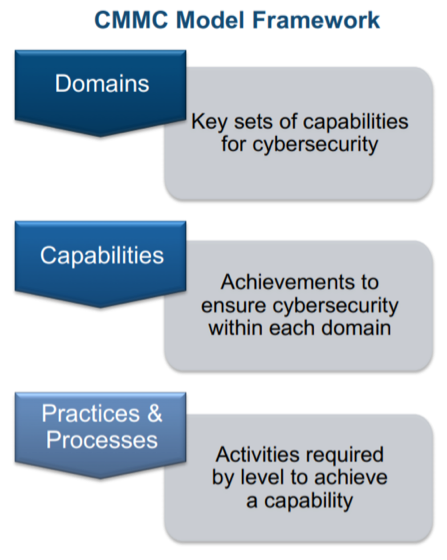
What does the Model Framework look like?
CMMC model framework consists of 18 domains, based on cybersecurity “best practices”. You could compare CMMC’s “domains” to the “families” of NIST 800-171. Inside these domains you’ll find capabilities which are comparable to the controls you would find in the NIST framework. Finally, capabilities are comprised of practices and processes, which are mapped to CMMC Levels 1 through Level 5.
To break that down, basically you have a group of 18 domains (families). Inside the domains are a number of capabilities (controls), and inside each capability are different practices and processes which are primarily activities required by level to achieve said capability.
– Practices are activities performed at each level of the domain
– Processess detail maturity of institutionalization for the practices
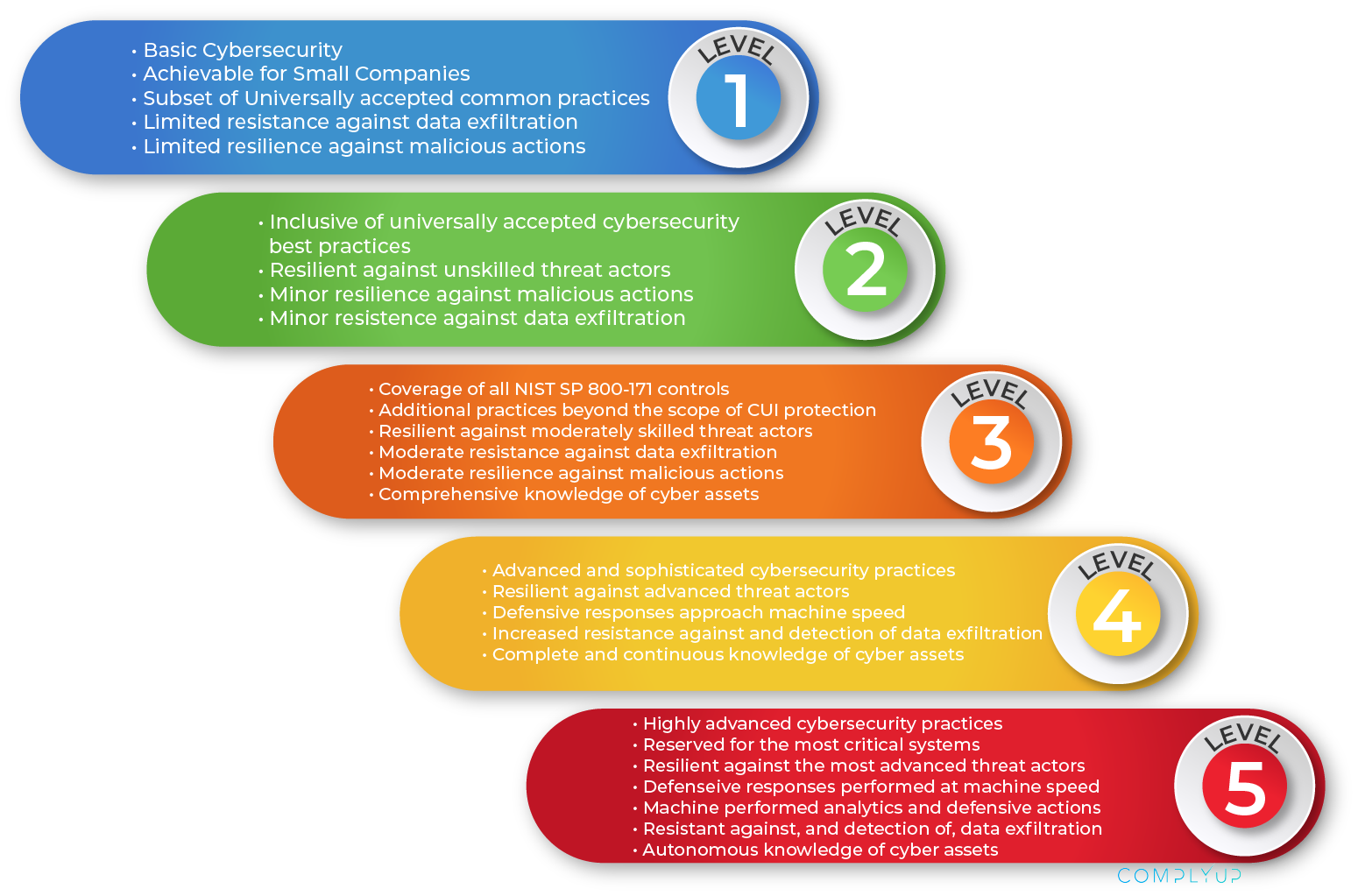
CMMC Model Level Descriptions
CMMC Model Rev 0.4 Levels by the Numbers
| Domains | Capabilities | Total Practices per Domain | Practices per Level | ||||
| Level 1 | Level 2 | Level 3 | Level 4 | Level 5 | |||
| Access Control | 5 | 30 | 5 | 9 | 11 | 5 | 0 |
| Assett Management | 4 | 19 | 2 | 5 | 7 | 5 | 0 |
| Audit and Accountability | 8 | 27 | 2 | 9 | 7 | 7 | 2 |
| Awareness and Training | 4 | 16 | 0 | 4 | 5 | 7 | 0 |
| Configuration Management | 5 | 21 | 2 | 8 | 4 | 6 | 1 |
| Cybersecurity Governance | 4 | 21 | 2 | 6 | 4 | 9 | 0 |
| Identity and Authorization | 2 | 17 | 2 | 1 | 9 | 2 | 3 |
| Incident Response | 9 | 41 | 3 | 15 | 7 | 9 | 7 |
| Maintenance | 2 | 9 | 1 | 5 | 2 | 1 | 0 |
| Media Protection | 8 | 13 | 1 | 6 | 5 | 0 | 1 |
| Personnel Security | 2 | 5 | 2 | 2 | 0 | 1 | 0 |
| Physical Protection | 5 | 17 | 4 | 10 | 3 | 0 | 0 |
| Recovery | 2 | 8 | 0 | 3 | 3 | 2 | 0 |
| Risk Management | 7 | 36 | 0 | 9 | 6 | 15 | 6 |
| Security Assessment | 6 | 15 | 1 | 6 | 2 | 5 | 1 |
| Situational Awareness | 4 | 17 | 2 | 2 | 3 | 7 | 3 |
| System and Comms Protection | 3 | 45 | 2 | 10 | 13 | 12 | 8 |
| Systems and Info Integrity | 5 | 13 | 4 | 5 | 0 | 2 | 2 |
| Total Practices Per Level | 35 | 115 | 91 | 95 | 34 | ||
The Difference Between Levels
Levels 1 and 2 are intended to provide basic cybersecurity standards that will include practices such as anti-virus, ad hoc incident response, awareness and training, risk management, and security continuity.
Level 3 will be required of any contractor who actually handles and stores CUI. It will include all NIST SP 800-171 Rev 1 requirements, an Information Security Continuity Plan and ensure you are able to communicate threat information to key stakeholders.
Levels 4 and 5 are targeted toward a small subset of the DIB (Defense Industrial Base) sector that supports DOD critical programs and technologies.
Timeline/Schedule
– Public comment of draft CMMC Rev 0.4 in September 2019
– Public comment of draft CMMC Rev 0.6 in November 2019
– CMMC Rev 1.0 will be released in January 2020
– CMMC will be included in RFIs starting in June 2020
– CMMC will be included in RFPs starting in Fall 2020
Important Notes to Remember
The model is still being refined and a reduction in size is anticipated. This means that they are still working out the kinks. Keep in mind the goal of CMMC is to be cost-effective and affordable for small business to implement the lower levels.
Detailed assessment guidance is still under development as well. They are planning on releasing a series of “Desk Books” to give concrete expectation for each CMMC level. These desk books will address both contractors and auditors.
Contractors can expect the desk books to spell out specifically what is required to obtain certification at a specific level, plus implementation examples where appropriate. On the auditor side, these books will clearly state what should be evaluated and how. This will ensure audit results are trustworthy regardless of the source.





