CMMC Model v1.0 has been Released
Published:
Feb. 4th, 2020
The wait is over. CMMC v1.0 is now available. Contractors can finally look at the first version of the model and begin assessing their systems against its requirements.
A lot has remained the same from Draft V0.7 but there are a few highlights we’d like to discuss as well as touch on some basics of the standard.
The Official Model v1.0 is available here.
The Model v1.0 Overview, Framework and Levels
Overview
The v1.0 document includes:
• The CMMC Model and Summary
• Appendix A: CMMC Model v1.0
• Appendix B: Process and Practice Descriptions
• Appendix C: Glossary
• Appendix D: Abbreviations and Acronyms
• Appendix E: Source Mapping
• Appendix F: References
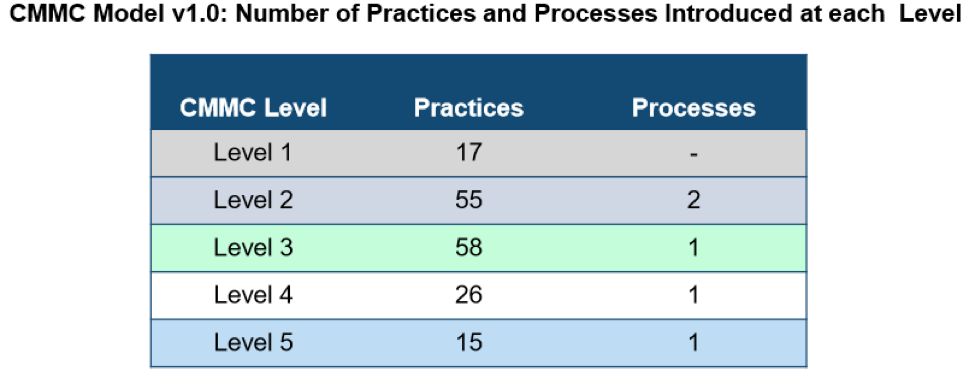
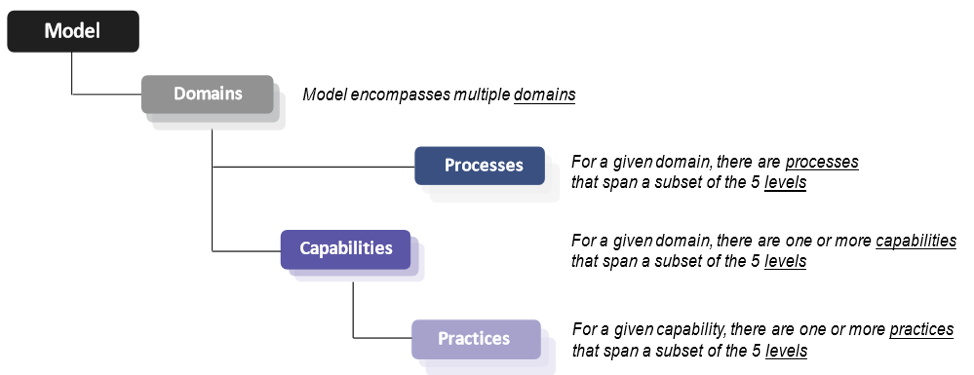
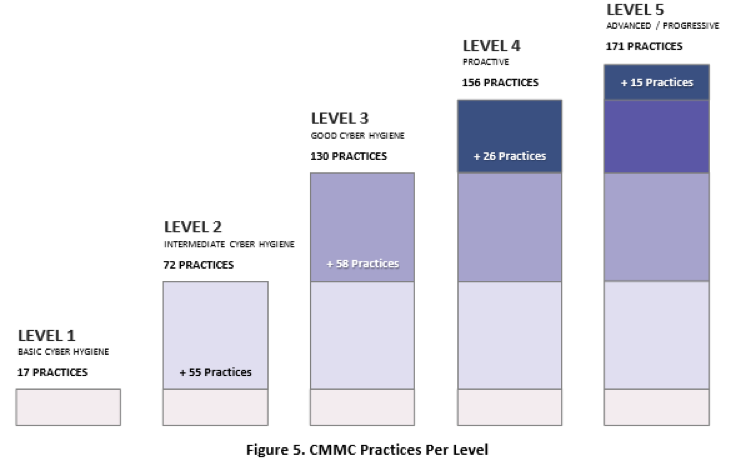
The final revision is comprised of 17 Domains, 43 capabilities, 171 practices to measure technical capabilities as well as 5 processes across the 5 levels (Levels 2 – 5) to measure process maturity.
Framework
CMMC combines processes and practices into a set of domains that map across 5 levels. These domains contain processes and Capabilities and those Capabilities contain Practices.
Levels
Level 1 Level 1 is for basic safeguarding of FCI (Federal Contract Information). It is comprised of 17 practices and has no processes in place. Level 1 only addresses practices from the FAR Clause 52.204-21.
Level 2 Level 2 is meant to be a transitional step form safeguarding FCI to protecting CUI. Level 2 contains 72 practices and 2 processes.
Level 3 Level 3 is for protecting CUI. It contains 130 practices including all 110 controls found in NIST 800-171 Rev.1. All contractors that handle CUI will be required to certify at a CMMC Level 3. This level also contains 1 process.
Levels 4 & 5 Levels 4 and 5 are aimed at protecting CUI and reducing risk of APTs. These levels contain an additional 41 practices (26 in L4 and 15 in L5). These practices are sourced mostly from NIST 800-171 Draft RevB.
| CMMC Level | Practices | Processes |
| Level 1 | 17 | – |
| Level 2 | 55 | 2 |
| Level 3 | 58 | 1 |
| Level 4 | 26 | 1 |
| Level 5 | 15 | 1 |
Practices and Processes
Appendix A includes the CMMC model v1.0 in tabular form with all practices organized by Domain (DO), Capability, and Level (L)
Practices are numbered as DO.L.###, with a unique practice number (###)
For example: The first practice found in the standard is listed in domain Access Control, under capability C001 Establish System Access Requirements. Therefore, it is listed as AC.1.001.
Appendix A also includes maturity level processes
Processes are generalized but apply to all domains.
Processes are numbered as ML.L.99#
The “ML” stands for Process Maturity while the “L” represents the CMMC level of that process. The numbers after the “L” are in reference to the 5 processes (ranging from 995-999).
Example:
Maturity Level 2 (ML2)
ML.2.999
Establish a policy that includes (DOMAIN NAME)
Practices
The model consists of 171 practices that are mapped across the five levels of capabilities and domains. Most of these practices originate from the safeguarding requirements and security requirements found in FAR Clause 52.204-21 and DFARS Clause 252.204-7012.
Level 1 is equivalent to all of the safeguarding requirements from the FAR clause.
Level 3 includes all of the security requirements in NIST 800-171 plus other practices.
Similar to how discussions and clarifications were included for Levels 1, 2 and 3 in Draft V0.7, the newest iteration includes discussions and clarifications for Levels 4 and 5 as well. These can be found in appendix B.
This appendix includes references, discussions from the sources, clarifications and examples of practices found in each of the 5 levels.
References
Each practice includes a reference. The reference refers to which standard or framework the practice can be mapped back to. For example, AC.1.001 can be referenced to a vast number of frameworks:
• FAR Clause 52.204-21 b.1.i
• NIST SP 800-171 Rev 1 3.1.1
• CIS Controls v7.1 1.4, 1.6, 5.1, 14.6, 15.10, 16.8, 16.9, 16.11
• NIST CSF v1.1 PR.AC-1, PR.AC-3, PR.AC-4, PR.AC-6, PR.PT-3, PR.PT-4
• CERT RMM v1.2 TM:SG4:SP1
• NIST SP 800-53 Rev 4 AC-2, AC-3, AC-17
• AU ACSC Essential Eight
Discussion from Source
The discussion sections found for each practice include the reasoning and breakdown of what is being required of your organization. Here’s an example of what that looks like for AC.1.001:
Access control policies (e.g., identity-or role-based policies, control matrices, and cryptography) control access between active entities or subjects (i.e., users or processes acting on behalf of users) and passive entities or objects (e.g., devices, files, records, and domains) in systems. Access enforcement mechanisms can be employed at the application and service level to provide increased information security. Other systems include systems internal and external to the organization. This requirement focuses on account management for systems and applications. The definition of and enforcement of access authorizations, other than those determined by account type (e.g., privileged versus non-privileged) are addressed in requirement 3.1.2.
CMMC Clarifications and Examples
CMMC Clarifications are provided to give guidance to how to apply the practice to your organization. The discussion is there to tell you what to do, while the clarification is there to tell you how to do it. The clarifications also include examples to give contractors a practical view of how to implement the practice. The examples are not meant for guidance but rather to help explain the practice. Here’s another example from AC.1.001 of what the CMMC clarification looks like:
Control who can use company computers and who can log on to the company network. Limit the services and devices, like printers, that can be accessed by company computers. Set up your system so that unauthorized users and devices cannot get on the company network.
Example 1
You are in charge of IT for your company. You give a username and password to every employee who uses a company computer for their job. No one can use a company computer without a username and a password. You give a username and password only to those employees you know have permission to be on the system. When an employee leaves the company, you disable their username and password immediately.
Example 2
A coworker from the marketing department tells you their boss wants to buy a new multi-function printer/scanner/fax device and make it available on the company network. You explain that the company controls system and device access to the network, and will top non-company systems and devices unless they already have permission to access the network. You work with the marketing department to grant permission to the new printer/scanner/fax/ device to connect to the network, then install it.
Processes
CMMC Draft v0.7 contained 9 processes, whereas, v1.0 contains only 5 processes found within Maturity Levels 2, 3, 4 and 5. The processes are in place to provide additional assurances that the practices associated with each level are implemented effectively. These processes apply to all domains:
| Maturity Level | Maturity Level Description | Processes |
| ML 1 | Performed |
There are no maturity processes asses at Maturity Level 1 An organization performs Level 1 practices but does not have process institutionalization requirements. |
| ML 2 | Documented |
Establish a policy that includes (DOMAIN NAME). Document the CMMC practices to implement the {DOMAIN NAME) policy. |
| ML 3 | Managed | Establish, maintain, and resource a plan that includes (DOMAIN NAME). |
| ML 4 | Reviewed | Review and measure (DOMAIN NAME) activities for effectiveness. |
| ML 5 | Optimizing | Standardize and optimize a documented approach for (DOMAIN NAME) across all applicable organizaion units. |
Appendix B includes references, source discussions and CMMC clarifications for all 5 processes. They do not include examples.
References
All 5 of the processes reference CERT RMM V1.2.
In example here are some references from ML.2.999:
– CERT RMM v1.2 GG2.GP2
– CERT RMM v1.2 GG2.GP3
Discussion from Source
Just like the discussions for practices, the discussion for processes also give insight into what exactly the process is expecting from you. Here’s an example from ML.2.999:
ML.2.999: Establish a policy that includes (DOMAIN NAME).
Discussion from Source: CERT RMM v1.2
Develop and publish organizational policy for the process.
Establish the organizational expectations for planning and performing the process, and communicate these expectations via poicy. THe policy should reflect higher level managers’ objectives for the process.
CMMC Clarification
This section will describe what specifically should be included in that policy, plan or procedure as well as what needs to be done to implement the process. Here’s another example from ML.2.999:
A policy is a high-level statement from an organization’s senior management that documents the requirements for a given activity. It is intended to establish organizational expectations for planning and performing the activity, and communicate those expectations to the organization. Senior management should sign policies to show its support of the activity.
At a minimum, the policy should:
– Clearly state the purpose of the policy
– Clearly define the scope of the policy: for example, enterprise-wide, department-wide, or information-system specific;
– Describe the roles and responsibilities of the activities covered by this policy: the responsibility, authority, and ownership fo (DOMAIN NAME) domain activities; and
– Establish or direct the establishment of procedures to carry out and meet the intent of the policy, include any regulatory guidelines this policy addresses.