Cybersecurity Maturity Model Certification
CMMC
Cybersecurity Maturity Model Certification
Current Version: v2.0
The CMMC, which has three levels of certification ranging from Basic to Advanced, was implemented to shore up the supply-chain.
The current DFARS clause does not require third-party assessments, contractors may self-attest that they have complied with NIST SP 800-171. CMMC 2.0, however, will include an amalgamation of self assessments, 3rd party assessments, and government-led assessments.

A New Version of CMMC
The interim rule, which was published in September 2020, was DoD’s implementation of its initial vision for the CMMC program (CMMC v1.02). Initially, CMMC was going to be phased in over a five-year period. Then, in March 2021, the department conducted an internal review of the CMMC program. It was then in November 2021 that the department announced CMMC 2.0 in an effort to reflect necessary changes discovered in the March internal review.
What’s the difference between the old CMMC and the new CMMC 2.0?
Do I need to receive a certification from a third-party organization still?
When can we expect to see a CMMC 2.0 requirement?
What’s Changed?
This new version of CMMC contains a slimmed down tiered model of only 3 levels of compliance/certification. Level 1 is considered Foundational and is the same as the previous model’s Level 1. Level 2 is “Advanced” and is equivalent to the older Level 3. Finally, Level 3 is “Expert” and is compared to the previous Level 5.
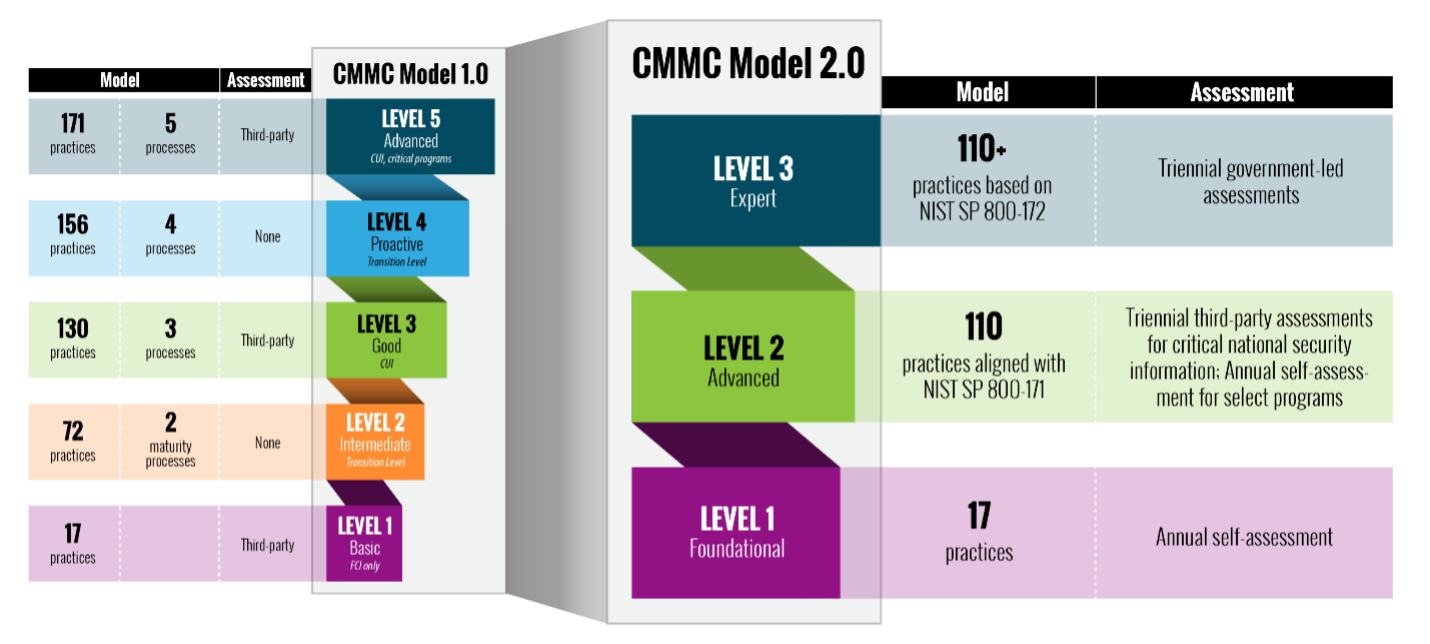
While Level 1 contains the same 17 practices, they’ve done away with the “delta 20” extra practices for Level 2. This means that the new CMMC 2.0 Level 2 contains 110 practices, each of which directly maps to the 110 controls found in NIST 800-171. They have also combined levels 4 and 5 into a single Level 3. Level 3 will contain all the controls mapped from NIST 800-172.
Another big change for CMMC 2.0 is the allowance of POA&Ms. In the previous version of CMMC an organization would not receive certification if it had any deficiencies. In the new version, they are allowing POA&Ms under certain limited circumstances. This means that, as long as you have plans to correct your deficiencies, you will be given the time to correct those and still receive your certification/claim compliance.
Finally, not every organization is going to need a certification to claim compliance. They are allowing ALL of level 1 and some of Level 2 to self-assess themselves. This is another big difference between CMMC 1.2 and CMMC 2.0.
Certification vs. Self-Assessment
Under the new CMMC 2.0, as mentioned above, not everyone is going to need a certification. Some will be allowed to self-assess; some will need a third-party organization to audit/assess them in order to receive a certification while a select few will be assessed and certified by the government itself.
So who will need what?
All of Level 1 will be permitted to annually self-assess. This will require some sort of documentation containing responses to each of the 17 practices found in Level 1. We’re not entirely sure of the process for claiming compliance yet but we do know that you’ll need to be able to prove that you self-assess your organization annually.
Level 2 will be split into two groups. Those who have been deemed to work with critical national security information will need to obtain a certification with a C3PAO. Those organizations will need re-certification triennially (every 3 years). Those who do not contain that information will be allowed to self-assess. Again, we’re not entirely sure what the self-assessment process will look like but we can be 100% sure that they will need a System Security Plan to claim compliance. Like Level 1, those self-assessments will need to be conducted annually.
*It’s worth noting that any organization that stores, processes or handles CUI will most likely fall under Level 2.
The select few that will need to obtain a Level 3 certification will be assessed by the government itself. Level 3 is made up of all the controls found in NIST 800-172 (the previous NIST 800-171B). There has not been much information released about Level 3 or the process of gaining certification by undergoing a government-led assessment.
What’s Inside?
To fully understand what we’re up against, some terms and structures need to be explained.
The CMMC, at a glance, looks a lot like NIST 800-171 in terms of the required security “requirements”. In fact, all 110 NIST 800-171 controls can be found in CMMC Level 2.
One difference to note, though, is that CMMC doesn’t use terms like “controls” or “families”. Instead, it uses terms like “domain” and “practices”.
At a simplified level, to illustrate the structure, we can make a few connections between NIST 800-171 and CMMC terminology:

The levels in CMMC are also a key differentiator from NIST 800-171. Levels are used to define the level of certification within an assessment ( more on that in the Levels tab ). Deciding the level of certification that you’re attempting to achieve is usually the first step when beginning a CMMC assessment. From there, you’ll need to implement the practices not only for your level, but for the lower levels as well.
Again, all the 110 NIST 800-171 controls can be mapped directly to CMMC Level 2 in the form of practices. To that end, as we await more answers and set dates from the Accreditation Body and OUSD, a safe bet would be to obtain 800-171 compliance. Not only will that take care of a huge portion of your CMMC assessment, it’s also the current contractual requirement under DFARS clause 252.204-7012.
Completing your NIST 800-171 assessment with ComplyUp will allow you to produce a System Security Plan, Plans of Actions and Milestones (POAMs) and generate your SPRS score. Those are the three key factors in claiming compliance to NIST 800-171. From there, you have the ability to purchase a CMMC assessment and, from within the platform, map and migrate your NIST assessment to your CMMC assessment.
Reach out to us to learn more about how to gain NIST 800-171 compliance and work towards your CMMC certification.
Certification
Obtaining CMMC certification has become a topic of much confusion and indirect information. Here are a few things that we know for sure.
- Currently (01/24/22), there is not a single CMMC certified company in existence.
- An organization called “The Accreditation Body” have begun the process of accrediting organizations and individuals who are able to provide the qualified assessments that can result in CMMC certifications.
- C3PAOs (which are the companies that will conduct and oversee individual assessments) have started to undergo their own CMMC level 3 assessments (under the older CMMC V1.02) conducted by the Defense Industrial Base Cybersecurity Assessment Center (DIBCAC). For these C3PAOs to start conducting assessments of contractors, they will need to pass their own assessments with DIBCAC.
- There are no official announcements as to which contracts will be audited first and therefore no knowledge of which companies will need to be CMMC certified.
- On a similar note, we’re still not sure how the assessments will be prepared, executed, or announced. There is a lot of controversial discussion around in-person assessments of contractor’s organizations as well as in-person assessments for work-from-home employees that will, according to the CMMC AB, be conducted at the individual’s personal home.
- No 3rd Party Organization, regardless of claim, has the ability to grant a CMMC certification yet. They can perform gap-assessments, prepare documents, create evidence, manage policies, and everything in-between, but they are not able to grant certification yet.
Timeline and Rulemaking for CMMC 2.0
CMMC 2.0 will take some time to make it into actual DoD contracts. It must first go through the rulemaking process. This involves DoD pursuing rulemaking both in Part 32 of the Code of Federal Regulations (C.F.R.) as well as in the Defense Federal Acquisition Regulation Supplement (DFARS) in Part 48 of the C.F.R. In addition to the time that will take, both rules will have a public comment period. In other words: It is unclear how long it will take for CMMC 2.0 to take effect. It has been estimated to take as long as 9 – 24 months until you see a CMMC requirement in any solicitation.
In the meantime, folks should be working on NIST 800-171. Growing the System Security Plan and shrinking the POA&Ms. ComplyUp can help with that.
ComplyUp consistently stays up-to-date with information on this subject. If you want to stay in-the-know, sign up for our CMMC mailing list.
We’re never spammy and we release the information as soon as we hear updates.
The CyberAB
The CyberAB (formerly CMMC Accreditation Body) is the organization that is responsible for operationalization of CMMC Assessments (Audits), accreditation and training of CMMC Provisional Assessors and C3PAOs. The CyberAB will select, vet, and accredit the individuals and organizations that will be authorized to conduct CMMC assessments (audits).
For more information on the CyberAB, visit cyberab.org.
Policies are an important part of any information security framework. They help organizations ensure that users of networks or infrastructures abide by the set of rules regarding the security of sensitive data.
Each CMMC subscription of ComplyUp ( starting at Level 2 ) includes the 14 CMMC domain-specific policy templates.
These were created by professionals, specifically to help customers satisfy those processes. Each policy template includes references to the individual practices located in the corresponding domain. These policy templates, coupled with the additional 25 information security best practice policy templates, can give your organization an excellent start to documenting your compliance journey and they’re included with your subscription at no extra cost.
Levels Overview
Cyber Hygiene:
Foundational
Certification:
Annual Self-Assessment
Security Practices:
17
Overview:
Practices – Level 1 focuses on the protection of FCI and consists only of practices that correspond to the basic safeguarding requirements specified in 48 CFR 52.204-21 (“Basic Safeguarding of Covered Contractor Information Systems”).
Cyber Hygiene:
Advanced
Certification:
Annual Self-Assessment or Triennial Third-Party Assessments.
Security Practices:
110
Overview:
Practices – Level 2 focuses on the protection of CUI and encompasses all the security requirements specified in NIST SP 800-171 as well as additional practices from other standards and references to mitigate threats.
It is noted that DFARS clause 252.204-7012 (“Safeguarding of Covered Defense Information and Cyber Incident Reporting”) specifies additional requirements beyond the NIST SP 800-171 security requirements such as incident reporting.
Cyber Hygiene:
Expert
Certification:
Government-led Assessments
Security Practices:
TBD
Overview:
Practices – Level 3 practices are TBD but will be based on a subset of NIST SP 800-172 requirements.
Domains & Capabilities
- Establish system access requirements
- Control internal system access
- Control remote system access
- Limit data access to authorized users and processes
- Define audit requirements
- Perform auditing
- Identify and protect audit information
- Review and manage audit logs
- Conduct security awareness activities
- Conduct training
- Establish configuration baselines
- Perform configuration and change management
- Grant access to authenticated entities
- Plan incident response
- Detect and report events
- Develop and implement a response to a declared incident
- Perform post incident reviews
- Test incident response
- Manage Maintenance
- Identify and mark media
- Protect and control media
- Sanitize media
- Protect media during transport
- Screen personnel
- Protect CUI during personnel actions
- Limit physical access
- Identify and evaluate risk
- Manage risk
- Manage supply chain risk
- Develop and manage system security plan
- Define and manage controls
- Perform code reviews
- Define security requirements for systems and communications
- Control communications at system boundaries
- Identify and manage information system flaws
- Identify malicious content
- Perform network and system monitoring
- Implement advanced email protections
| Total Practices Per Level | Lvl 1 | Lvl 2 | Lvl 3 |
| 17 | 110 | TBD |
14 CMMC Domain-Specific Policies 2
Multiple Users
POA&Ms
Progress Visualization
2FA
Task Assignment
SSP Revision History
Bottom Line – We couldn’t decrypt your data if we wanted to.
By Contractors
The Cybersecurity Maturity Model Certification is a new standard that will take the place of NIST 800-171 on DoD contracts. CMMC 2.0 is broken down into 3 levels of certification ranging from basic to advanced.
Yes. Version 2.0 is available at https://www.acq.osd.mil/cmmc/.
Somewhat. All 110 controls found in NIST 800-171 can be found within CMMC. In fact, CMMC 2.0 Level 2 practices are mapped directly from NIST 800-171. Still, there are differences between the frameworks. CMMC has levels of certification, whereas NIST 800-171 is a “one-size-fits-all” framework. CMMC also requires a third-party assessment and certification on a subset of Level 2 contracts.
Existing DoD contracts that contains the 252.204-7012 DFARS clause will still require your organization to provide documentation proving compliance with 800-171. We don’t know if Contracting Officers will be asked to modify active contracts to swap CMMC and 800-171. This may end up being a per-contract decision. CMMC is different than NIST 800-171, but the controls can be mapped from 800-171 to the levels of certification within CMMC.
Yes. All companies doing business with Department of Defense will need to obtain CMMC. All of Level 1 requirements as well as some of Level 2 will need to complete an annual self-assessment, while the rest of Level 2 and Level 3 will need to undergo either a third-party assessment (a subset of Level 2) or a government led assessment (Level 3).
Even if you are a subcontractor.
We’re not sure yet. This will depend entirely upon what level of certification your contract requires and the sensitivity of the information you handle. We can say this: ALL companies handling CUI can expect to need to certify at a CMMC Level 2 certification (which will include all 110 controls from NIST 800-171) at a minimum. Level 1 will be required of companies that handle FCI (Federal Contract Information) while Level 2 will be required by most companies that handle CUI, and 3 will be required among a small subset of contracts handling extremely sensitive information. The safe bet at this point is to shoot for a Level 2.
1. Get NIST 800-171 documentation out of the way. This will get you through many of the CMMC Level 2 requirements and keep you compliant with the current DFARS clause.
2. Be ready to address any gaps you find and implement solutions to remediate them. It is still unclear whether your organization will need to obtain a third-party audit and certification or if you’ll be able to self-assess and submit the results manually.
Level 1 and Level 2 self-assessment’s will need to submit their results annually. A subset of Level 2 as well as Level 3 will need to undergo triennial assessments led by third-party organizations or the government itself.
We can’t say for sure. That depends entirely on the market. The Dod has made it clear that they are trying to keep the cost down and are encouraging industry to automate as much of this process as possible. ComplyUp is taking that approach and applying it to our business model. Our software is cost-effective and practical. The cost and associated assessment will likely scale with the level requested. It’s difficult to know exactly what the entire process will cost so it is important to do some price-shopping when selecting solutions and services.
By Assessors
You will need to become an accredited 3rd party commercial certification organization.
You can find more information on how to accomplish this at cyberab.org.
An organization called the CyberAB. This is a non-profit organization that has signed an MOU with the DoD and is the entity vetting and selecting C3PAOs.
You can find more information on how to accomplish this at cyberab.org
No. They have made it quite clear that they do not want the organizations who are performing the audits to also be the ones implementing the CMMC requirements for the contractor.
Like NIST 800-171, it is a requirement of CMMC to provide a System Security Plan as well as policies and procedures on how you implement the practices found in CMMC. The auditor will most likely need to provide a Report on Compliance, like that of PCI and FedRAMP. If you are submitting a self-assessment for Levels 1 or 2 you will need a System Security Plan to claim compliance.
Yes. If you want to be a successful CMMC auditor, it is important to keep the same goals in mind as the folks pushing CMMC. They want this to be cost-effective. That means we’re not dealing with a whole lot of “enterprise” customers here. We’re talking about the ENTIRE DoD supply chain, most of which are small businesses. In order to play ball, you’ll need to keep your cost low and keep the process somewhat automated.





